The old proverb “humans are the weakest link” remains truer than ever for cybersecurity projects. As cybercriminals continue to target remote workers, employee training highlighting social engineering has become essential. According to Tim Sadler, CEO of cybersecurity firm Tessian, “the easiest way into an organization is by tricking an employee into letting you in.”
Unsurprisingly, cybersecurity is a top concern for today’s organizations, institutions, and civilians. However, there are numerous organizations and people within who are susceptible to cybercrime, notably big corporations. One of the most prominent online threat to both consumers and businesses is phishing. These scams are almost as old as email itself, despite significant cybersecurity advancements, they continue to work.
Uber recently disclosed they have encountered an unfortunate circumstance, becoming the target of a strategic cyber attack. See tweet.
They reported that the hacker is an 18-year-old script kiddie. The focus of this blog is, what exactly occurred in this breach and strategically what could have been followed to prevent, detect, respond or recover from this.
Note: The sequence of events is written from public information available on the breach.
Phase 1: Initial Breach
Situation
On Thursday, September 16th, Uber confirmed reports of an organization-wide cybersecurity breach. The hacker claimed, the breach was set up by spamming an Uber’s IR employee for more than an hour with push authentication requests before using a different channel to deceive the employee into approving one of the requests

Prevent: Enhanced user training against social engineering attacks like phishing is one of the numerous preventative measures that may have been used. Although MFA can resist social engineering, man-in-the-middle attacks are still possible. A preventative measure may have been to adopt a robust MFA like FIDO2.

Detect: MFA alerts needed to have been sent from the server to the SIEM system, and the multiple push notifications could have been stopped after a certain number of tries from the application, allowing for early discovery of this compromise.

Respond: Companies should begin implementing phishing-resistant MFA, such as FIDO2, and they should put in place a rule that flags an account for reconsideration if the number of authentication requests exceeds a certain threshold.
Phase 2: Lateral Movement
Situation
The hacker then went on to use the employee’s VPN to pivot the internal network. He then started to scan the internal network for any useful information. Compared to external infrastructure, internal infrastructure is often significantly less audited and evaluated.

Prevent: Stronger network controls should be there both internally and externally. MFA must always be required for VPN too. Segmenting the internal network and dividing it into multiple zones is important. It is also crucial to implement a security module for identifying any suspicious activity. Any login from any non-registered device should be taken care of immediately.

Detect: If an unusual login occurs, SIEM should issue a warning, and if any suspicious activity is discovered, it should also notify the security team. Furthermore, if the attacker ran port scans or was rapidly accessing files, folders, and network areas, these may also be captured by the SIEM tools.

Respond: The session should have been suspended or terminated for logging in from an alien device or for unusual activity for that user. In addition, a complete activity trace would help identify where an attacker might have been.
Phase 3: Enumeration Phase
Situation
While scanning the environment, the hacker found some PowerShell scripts. One of the scripts contained the login information for a Thycotic (Now Delinea) PAM admin user. He used those credentials to extract secrets of Uber’s DUO, AWS, GSuite, OneLogin Environments and compromised them. Although these are some extreme claims from the hacker, he provided some screenshots of the actual environments in his multiple interactions.

Prevent: Perform user training for best practices for developing scripts. The admin account should have also used MFA and alerting features whenever it was used. Within the PAM solution, segregation of duties should be there so that the administrator account can also not access all the privileged accounts. Finally, any login using that account should use a workflow for approval and any circumvention should raise alarms.

Detect: A flag for alerts may have served as a warning when the Administrator user logged in. The privileged accounts themselves (DUO, Google, HackerOne, etc.) should have had alerting and approval workflows in place to prevent untoward access. There is also a feature in Thycotic (Now Delinea) to “Double lock” these sensitive accounts i.e. entering another password tied only to the user locally, that can be used for additional authentication.

Respond: Once detected, disabling of compromised accounts could have been carried out. Admins must monitor the logs for any export that may have happened. Furthermore, a reset of privileged accounts must be undertaken so as to reset any passwords and the PAM system must be locked down from all users while a preliminary investigation is undertaken.
Phase 4: Breached
Situation
The hacker appears to have identified himself to Uber’s staff members by sending a message on its internal Slack platform: “I announce I am a hacker and Uber has suffered a data breach,”. The Hacker also mentioned a hashtag at the end of his message which says “Uber underpays its drivers”.
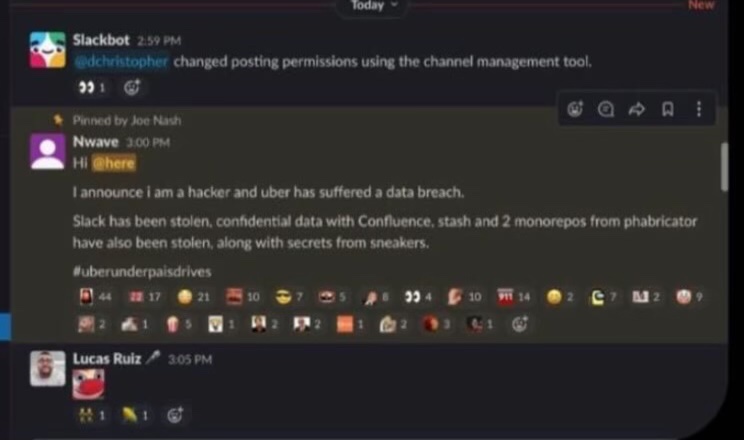
Sam Curry, a security engineer at Yuga Labs, was told by an unnamed Uber employee that employees were interacting with the hacker under the impression that they were making a joke. See Tweet.
It is concerning that the attackers seem to have gained access to an account belonging to an IR team member. “This is a total compromise, from what it looks like,” Curry told the New York Times. “It seems like maybe they’re this kid who got into Uber and doesn’t know what to do with it, and is having the time of his life.”

Respond: After a breach has occurred it’s crucial to first secure compromised systems. All teams must assist in this coordinated effort led by an Incident Response team. Furthermore, customers, vendors, and partners must be kept in the loop to reduce reputational damage. Law enforcement agencies must be contacted and kept in the loop to provide assistance where required and help identify the attacker.
Recover: Once core business operations and critical systems are back up the teams must identify what the impacts of the breach were. A detailed incident summary must be prepared along with controls that can help prevent it. Based on this and any identified gaps, the organization must undertake efforts to improve people, process and technology to help reduce the chance of further breaches.
Conclusion
This was not the first time Uber had a data breach. Hackers had already taken data from Uber. Hackers stole data from 57 million driver and rider accounts in 2016, and when Uber was contacted, they requested $100,000 to get rid of their copy of the data. Uber handled the money but hid the breach for almost a year.
The hacker in this case was significantly assisted in carrying out such a major infiltration by the responsiveness of the employees. As businesses adjust their cybersecurity practices to protect themselves in a hybrid-work world, executives should keep in mind that it is a continuous improvement process. Organizations may require a security gap closure initiative, but security awareness should be embedded throughout the business at all times. “Cybersecurity needs to be a part of the organization’s fabric.”
How can SecurDI help in securing your environment?
SecurDI can assist in assessing your current environment to find gaps in various cyber security areas-. With our certified professionals, we can assist you in building a robust and resilient cyber security posture. We cover the complete spectrum of People, Process, and Technology so that the organization is safe and secure. Our goal is to assist you as a trusted advisor for the duration of the project and beyond.

