The Internet of things(IoT) has fast grown to be a large part of our lives. Smart home devices like Alexa and Google, smart automobiles with built-in voice assistants, industrial sensors, industrial robots, fitness devices, smart cameras, smart locks and the list is endless. These devices come with a great branding and huge market influence, but they leave several questions unanswered.
- Are they really secure?
- Can they be trusted?
- Do they implement the best compliance standards?
Sadly, the answer to these questions is ‘No’. Anything connected to the internet is susceptible to threats.
IoT devices have various inadequacies in their system. Every system comes with its pros and cons. Scalability, simplicity, and portability can be pros but security issues that often lead to some bigger problems might pose a threat. So, here are some common threats in IoT devices:
- Data collection: Pick any fitness device or google assistant or industrial sensors – What will you find? Abundance of personal data. Fitness devices have your heart tracking, google assistant has everything, and industrial sensors reveal a lot about the industry. So, if you lose your device or even dump it without proper care then eventually your data is exposed to everyone.
- Improper configurations: Many IoT devices lack proper configuration techniques just like a smartphone which has tons of bloatwares. Anything connected to the internet is prone to vulnerability and due to improper configurations this makes it an even bigger threat.
- Weak passwords: IoT devices come with a default password and very few of them change to a custom password. It’s a simple step but still users delay it by compromising their device security. The more complex the password is, the more difficult it is to crack.
- Lack of regular patches: IoT devices are developed with ease of use. They may be secure at the time of purchase but as time progresses most of them don’t roll out updates/patches. After a year or two, it is common for hackers to find vulnerabilities in these devices and before you know it your device will be in the wrong hands.
- Network Communication: Protocols used in IoT systems can have security issues that can affect the entire system. IoT systems are also susceptible to known network attacks such as denial of service (DoS) and spoofing.
What do reports say?
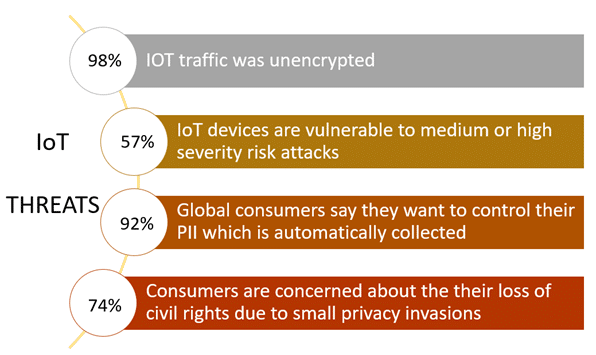
There are ways to tackle these threats by following best practices. The truth is “Privacy/Security is a myth”. When you buy a device, you need to ensure that you are using it efficiently and maintaining it by customizing it to your needs. Here are some best practices you can follow:
- Use strong and unique passwords for all accounts including admin accounts
- Prioritize Wi-Fi security an secure your networks with firewalls
- Regularly check for patches and updates, running on an outdated version is always an open invitation to the vulnerabilities
IoT devices are not secure, but we can make them secure by following some easy steps. This helps protect user data and the sensitive devices themselves. Following these steps will help reduce the attack vectors and allow seamless performance for a user and their device.
– Authored by Atharva Ratnakar Kulkarni
Pic Credits : Business photo created by jannoon028 – www.freepik.com

