Introduction
Many big organizations like SolarWinds, Colonial Pipeline, and Uber were the victims of cyber attacks even with well-managed security infrastructure. Smaller organizations are constantly under threat and vulnerable due to the lack of proper security infrastructure.
But in certain cases, an organization with a proper defense strategy has been able to overcome the attack in a short amount of time and with less damage. An appropriate strategy of defense not only means having security tools implemented, but it also involves educating your employee about common cyber threats. There are scenarios where organizations with the best security practices have panicked. Incident Response Plan helps with the steps an organization should follow during a Cyberattack.
What is an Incident Response?
Incident response is an organization’s way of detecting and responding to cyber-attacks and breaches. The purpose of incident response is to minimize the damages and reduce the recovery cost and time.
Need for Incident response?
Any cyber attack that hasn’t been properly contained and remediated may cause the organization to lose data, expose sensitive information, and damage an organization’s reputation. To better prepare for both the known and unknown, an organization must have a defense strategy to overcome breaches or cyber-attacks in a minimal amount of time. Thus, they can better spot security incidents as soon as they happen.
Even though organizations cannot eliminate the possibility of cyber-attacks, their incident response plan will help them to minimize the risk and damages.
Incident Response Plan:
The incident response plan describes the organization’s method, procedure, and guidelines to follow when an incident happens. It also helps understand the known and unknown attacks and how to remediate them. It has a predefined set of instructions to detect, analyze, and overcome such incidents with minimal consequence.
IRP must include the following details:
- Security team’s approach to the attack
- Security solutions – software and hardware that needs to implement across the enterprise
- A detailed explanation of what needs to be done in each phase
- Roles and responsibilities of each member of the incident response team
- Proper communication plan for the employee, customer, and law enforcement about the incident
The Computer Security Incident Response Team (CSIRT) is in charge of dealing with incident response and handling all security incidents affecting an organization.
How to respond to a cyberattack?
There are a total of 6 steps that happen in a cycle whenever an attack has happened.
- Getting prepared
- Identifying the incident
- Analysis
- Containment
- Eradication & Recovery
- Post-incident review
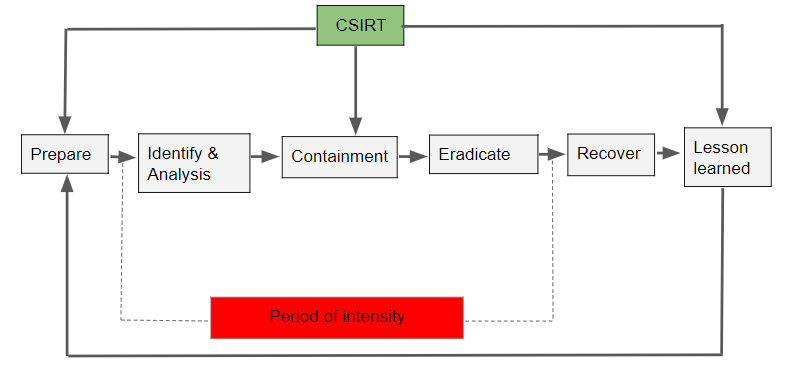
Preparation:
An organization cannot create an incident response on short notice. It should be a well-planned practice to prevent and respond to the incident. Preparation also refers to whether the organization’s security team has the proper tools and technologies in place to identify, contain and respond to the incident as quickly as possible.
Identification:
This step involves identifying whether an incident has occurred, the severity of that incident, and its type.
- Monitor: The security team monitors the network for any malicious activity or threats using a firewall, IPS, etc.
- Detect: Detect any potential incident by analyzing the data generated from the log or any alerts from the SIEM solution
- Report: Once all the false positives have been eliminated, the security team responsible for containing the incident must get notified of the incident.
Analysis:
Once the attack or the incident is identified, the security team should focus on these areas
- End-point analysis: Try to find the track left behind by the attacker. Collect the evidence that you will need to build the timeline for the attack.
- Behavioral Analysis: Run the malicious program in a virtual machine to observe how it behaves.
- Static Analysis: Reverse engineer the malicious program to scope out the entire functionality.
- Enterprise hunting: Analyse current systems and event log technology, so that containment and neutralization can be carried out effectively and keep track of any compromised accounts, devices, etc.
Containment:
The security team takes appropriate action to stop the incident and denies the threat from spreading to new areas.
- Short term containment: Immediate threats are isolated in place.
Example: An attacker’s current location on your network can be isolated. It can be achieved by making certain sub-networks offline and relying on backups to maintain operation. - Long Term containment: Applying additional security measures to the unaffected systems. Terminating the attacker’s presence or activity from all parts of the network – infected system, malware, compromised user accounts. Taking preventive measures to make sure it doesn’t happen again.
Eradication & Recovery:
Once the threat is contained, the security team should move to full remediation, which typically involves deleting the malware or removing the unauthorized user from the network.
When the threat is neutralized, the system switches to its normal operation. This involves applying security patches, securing the network, building up the system from backups and restoring the device online.
Post-Incident Plan:
An incident review meeting with every member of the Incident Response Team should be held. When the investigation is finished the procedures should be documented and archived for future reference.
Example:
A hospital’s ex-employee in Valdosta, Georgia, downloaded private data from the South Georgia Medical Center to his USB drive. This is an example of a malicious insider threat in which the insider was angry, dissatisfied, or had personal reasons to harm the organization.
A former employee illegally accessed data from the South Georgia Medical Center and faced no obstacles in carrying out his plans. However, South Georgia Medical Center’s security software detected the incident and alerted cybersecurity personnel in response.
Examples of internal data breaches like this indicate that the organization was targeted and had monitoring software installed. In the case of South Georgia Medical Center, the incident was discovered and resolved quickly. However, effective access management tools, combined with access permissions-based tools, could have prevented unauthorized access from the start. A privileged access management solution could have helped to avoid this incident.
“Prevention is better than cure” But why worry about the disease when you have the cure? Similarly, when you have the first line of defense implemented in your organization, you can be certain that damages and consequences are low.
How SecurDI can help?
At SecurDI, we assist organizations in improving their operations by standardizing and simplifying the whole lifecycle of cyber security services. We review their existing plans and capabilities and then work with their team to build standard operating procedures. We guide them to handle the account and set up the organization’s infrastructure to protect against threats. However, to find a tool or technology that serves as the solution for the company and addresses all security requirements while also providing better management, you will need a team of professionals with expertise in various domains who can help and guide you through the process of finding and implementing the best fit solution. SecurDI can help mitigate cyberattacks by implementing cyber security solutions for your needs with our experienced professionals.
Authored by,
Balaji Chandrasekaran

