In the last several decades, digital technology has transformed practically every area of people’s life. Some of the sectors that have been revolutionized include entertainment, education, communication, and especially IT. Given the epidemic, practically everything has gone virtual since then. Now-a-days we can see that our daily life depends on technology more than it has ever been.
Considering the pace at which we are all moving, organizations are constantly striving to connect everything digitally. Among many such sectors involving technologies, IoT is one such consistent and ever-evolving sector.
The Internet of Things (IoT) is a concept that refers to a system of physical products, or rather “things,” that are equipped with sensors, software, and other capabilities to communicate and exchange data with other equipment and systems over the web. The “internet of things” was made possible by the fact that nearly any device we use today can be connected and interconnected, whether it be one we use in our homes, offices, businesses, or even just carry around with us. Ericsson forecasted that by 2022, a total of over 29 billion of these gadgets will be operating worldwide, and that number would continue to rise.
The IoT holds a considerable amount of user data due to the large number and variety of “things” that make up the network. Cybercriminals can potentially steal or hack all of this information. The more linked gadgets there are, the greater the chance that attackers may jeopardize one’s security. Such instances will have negative consequences. Hence it is highly significant to secure the devices in the network, which paves the path for cyber security. According to Gartner, currently, 40% of smart home appliances globally are being used for botnet attacks.
In the context of the aforementioned, it may be concluded that cyber security plays a crucial role in IoT since a single attack or breach might force the network to crash, or even worse, enable a cybercriminal full access to the system. In sectors like defense or military, IoT contains exceedingly critical information, and an attack on such sectors will not only be used to retrieve information but also cause physical damage to the entire network. The convenience and affordability that IoT offers are what most businesses and organisations are mostly focused on. As a consequence, they frequently ignore the dangers that come with an increasing network. Some examples of major breaches are:

2021: Verkada Attack:
Around the month of March, a bunch of hackers were successful in gaining control of security camera feeds which are developed and managed by Verkada, an organization that sells security as a service. The reason for this breach was not because cyber security measures were not in place but in fact their scope was very limited.
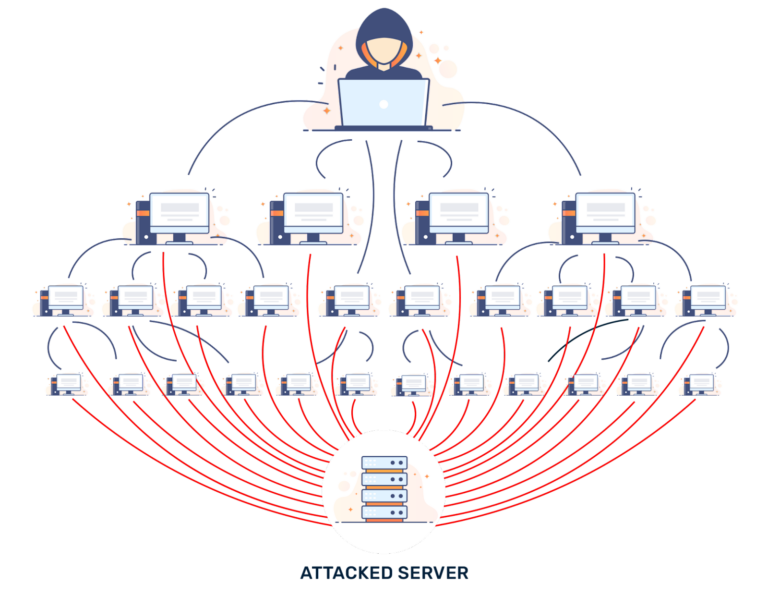
2016: The Mirai Botnet (aka Dyn attack):
This was considered to be one of the biggest DDoS attacks. Through widespread distributed denial of service assaults, Mirai (a malware) momentarily disrupted several well-known services using IoT devices such as cameras, routers and other devices. It was done in a simplistic yet smart approach of exploiting unsecured IoT devices by looking for open Telnet ports and logging in using the standard password.

Best Practices:
As it is rightly said that prevention is better than cure and this is more apt in any digital space. Therefore, it is very important to follow best practices and enforce good policies for the technology installed. Some of the best practices for IoT are:
- Be sure NOT to use the default passwords that many IoT devices come with. Since the standard passwords are weak they can be easily exploited and become a victim of brute-force attacks. Updating passwords and credentials regularly is a crucial step in maintaining excellent password management and should be handled to keep your devices safe at all times.
- Have regular software updates for the devices as out-of-date gadgets can be an easy target for hackers to exploit or hack into. IoT device security requires regular software upgrades.
- Use updated encryption protocols for general communication and especially when it deals with sensitive information. As this renders network data unintelligible to intruders.
- Securing the endpoints in the network. An additional endpoint joins the network whenever an IoT device is connected which in the future can become an entry point for hackers, hence it is necessary to protect them. As devices are constantly increasing it can become a cumbersome task to manage each device. Firms must use anti-virus software to better comprehend and enhance endpoint security.
- Have periodic audits of all the connected devices in the network as this can give an overview of the security status of the network. This method can detect incidents in their early stages. One should monitor for odd behaviours and abnormalities by keeping a log of activity and metrics.
- Network segmentation helps to separate the network into device groups based on policies that will control which devices have access to which data or application. The added benefit of this is that it lessens the congestion on the network.
- Having a proper IoT network firewall plays a vital role in securing the network, as the firewall defends the network devices from threats and also attacks. Firewall rules for both incoming and outgoing traffic will provide a security layer for the network on the whole.
Given today’s scenario there is a strong requirement for a reliable and robust security system and this requirement grows along with the expansion of digital technologies and linked devices. Good cyber security practices are essential when implementing an IoT interface. So it is justified to say that the Internet of Things without incorporating cyber security is an internet full of risks.
How can SecurDI help?
We assist our customers to secure their digital assets by understanding their needs and delivering the required service specific to them. By understanding the existing environment, we suggest solutions in accordance with it so that it is more feasible and effective. In order to suggest the best solutions for your digital security we have professionals with industry experience as well as certified to provide the best service.
Reference: https://www.ericsson.com/en/reports-and-papers/mobility-report
Authored By,
Kiruthika Palanikumar

