Data security in the cloud is highly relevant and crucial in today’s digital landscape. With increasing cloud adoption, remote workforce and cloud dependence along with the continuously evolving threat landscape, spreading awareness and investing in robust data security measures is a proactive way to ensure safe data in the cloud.
Data security in the cloud requires a different approach than the traditional cybersecurity strategies. Security models in the cloud should align with the evolving risks associated with cloud computing.
Common risks surrounding cloud data security:
Data Breaches:
A Cloud Security Report in 2022 revealed that 27% of businesses had encountered a security breach in their public cloud infrastructure over the past year. Data breaches involve unauthorized access to sensitive information stored in the cloud. Data breaches occur differently in the cloud than in on-premises attacks, IT security experts need more complex and aligned models to safeguard against such attacks.


Data Interception and Man-in-the-Middle Attacks:
Data Interception can occur through various means, such as eavesdropping on network traffic, DNS spoofing, or exploiting vulnerabilities in encryption protocols. These attacks can be positioned where there is communication between users and cloud services, inter-service communication within the cloud infrastructure, or communication between different cloud environments. MitM attacks can lead to severe consequences, including unauthorized access to sensitive data, theft of credentials or sensitive information, manipulation of data or transactions, and potential privacy breaches.
Unauthorized Access and Insider Threats:
Organizations depending on cloud environments tend to rely on access controls provided by the cloud service provider, which becomes an issue particularly in a multi-cloud or hybrid cloud environment. Lack of proper access controls can lead to insider threats such as unauthorized access, data leaks, data loss, intentional data exfiltration, deletion and manipulation. A 2023 report on Insider Threat states that 74% of organizations are at least moderately vulnerable to insider threats.


Insecure Interfaces and APIs:
Improperly configured interfaces and APIs can create security vulnerabilities. Businesses often rely on APIs to interact with cloud services, which increases the risk of attacks.
Other than data leaks or unauthorized access, some serious risks include injection attacks, cross-site scripting (XSS), and cross-site request forgery (CSRF). All these can lead to reputational damage, business interruption and financial losses.
Compliance and Legal Risks:
Compliance and legal risks are crucial considerations when it comes to cloud data security, as failing to adhere to applicable laws and regulations can cause severe consequences for the organization. The primary concern being data privacy and protection, the organization must ensure to comply with applicable data protection laws such as General Data Protection Regulation (GDPR) in the European Union, the California Consumer Privacy Act (CCPA) in the United States or the laws mentioned in The Information Technology Act, 2000 in India.

Best practices for risk mitigation:
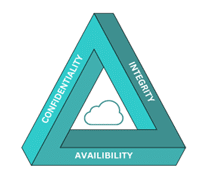
The core principles of information security (known as the CIA triad)—also apply to the cloud:
Confidentiality: Protecting the data from unauthorized access and disclosure.
Integrity: Safeguard the data from unauthorized modification so it can be trusted.
Availability: Ensuring the data is fully available and accessible when it’s needed.
Key strategies for securing your data in the cloud:
Strengthening IAM Infrastructure: A well built IAM infrastructure safeguards the cloud data storage and transactions by establishing centralized user management, granular access control and RBAC(Role-based Access Control), Identity Lifecycle Management and strong authentication to cloud services.
Advanced Encryption: Data should be encrypted both in transit and at rest. Implementing advanced encryption mechanisms on the client’s side along with the default encryption options provided by the cloud service providers helps protect data even if it is compromised or accessed without authorization. Key management services like AWS Key Management Service (KMS) and Microsoft Azure Key Vault, enables us to create and control the encryption keys used to encrypt your data on the respective platforms..
Data Backup and Disaster Recovery: Ensuring regular data backup and establishing an effective data recovery plan helps in situations where crucial data has been corrupted or lost. Data backup and recovery plan also ensures that there is no interruption in business operations due to data loss. Cloud services like Google Cloud Storage and Microsoft Azure provide backup and recovery services by implementing backups, data compression, geo-redundancy and flexible retention policies.
Strong Authentication Layers: Multi-level authentication to cloud services prevents unauthorized access to some extent even if there is credential leak. For example, MFA(Multi-Factor Authentication) including OTPs, biometric authentication, and hardware authentication, enhance security level for user authentication.
Regular Security Audits and Security Assessments: Identifying vulnerabilities in a cloud infrastructure, applications, and configurations can be done by regular security audits. This can be used in turn to fix the weaknesses that can lead to data breaches in the future. Security Assessments for the CSPs are done to evaluate the security certifications, compliance with standards and incident response capabilities.
Implementing DLP Tools: A Data Loss Prevention (DLP) tool is a security solution designed to prevent the unauthorized disclosure or loss of sensitive data. These tools help identify, classify, monitor, and protect sensitive data, enabling proactive detection and prevention of data breaches, unauthorized access, and data leakage incidents.
What did we learn?
In conclusion, we learned that data security in the cloud is a critical concern for organizations and individuals alike, given the evolving landscape of cyber threats and increasing reliance on cloud services.
Although, with proper adoption of comprehensive and proactive security approaches, one can easily mitigate the security risks existing in today’s cyber environment.
How can SecurDI Help?
Our teams of seasoned professionals at SecurDI have years of experience in providing outstanding security solutions over several organizations. They offer an array of services including implementation and management of strong access management solutions, security assessments, addressing concerns raised during the assessments and more, keeping your organization safe and secure on the cloud.

