Introduction
Logging onto a website or service with the usual username and password combination is no longer the best or safest method. Data protection measures must improve with the ever-evolving cyber criminals. This is where new authentication protocols like FIDO2 will help
But what exactly are the FIDO2 specs and requirements and how does the FIDO2 standard work? In this extensive introduction, we’ll address these and many other important questions about this password-less authentication standard.
New Password less Standard: FIDO2
FIDO2 (Fast Identity Online) builds on previous work by the FIDO Alliance, particularly with regard to the development of the Universal 2nd Factor (U2F) authentication standard. It is the third standard to emerge from the FIDO Alliance, after FIDO Universal Second Factor and the FIDO Universal Authentication Framework. The main goal of FIDO2 is to eliminate the use of passwords on the Internet. It was developed to introduce open, royalty-free standards for secure authentication worldwide over the Internet. The FIDO2 authentication method substitutes the typical hazards associated with the username and password login with the password-less FIDO2 login standard, which eliminates the traditional threats associated with username and password login. As a result, it safeguards against typical online threats such as phishing and man-in-the-middle assaults.
How Does FIDO2 Work?
This standard integrates public-key cryptography to ensure a safe and user-friendly authentication. you must first register at a FIDO2-compatible site” a private and public key pair to validate each user’s identity. To utilize FIDO2 authentication, you must first register at a FIDO2-compatible site. The following set-up steps are required for to begin with:
- You must complete the proper registration form and select a FIDO2 security key .
- A FIDO2 authentication key pair will be generated by the service.
- The public key is sent to the service by your FIDO2 device, while the private key containing sensitive information remains on your device.
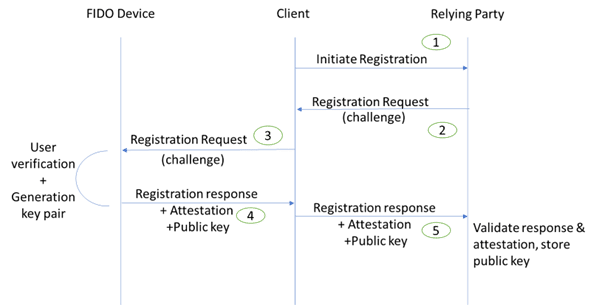
FIDO 2 Registration
The setup credentials are saved permanently after the secure communication method is activated, enabling future logins. You must do the following procedures the next time you wish to log in to a FIDO2 service:
- Enter your login and email address.
- You will be sent a cryptographic challenge from the service.
- You sign the challenge with your FIDO2 key.
- The server of the service validates your response and grants you access to your account.
It’s crucial to note that you don’t trade any secrets with the servers throughout this secure online log-in procedure. The critical piece of information, your FIDO2 private key, is always stored on your device.

WebAuthn Diagram – FIDO 2
FIDO2 vs FIDO vs WebAuthn
While they sound similar, FIDO2 is not the same as FIDO. It is also distinct from WebAuthn.
FIDO2 vs FIDO: FIDO is an umbrella name that refers to the FIDO Alliance or all FIDO standards such as UAF (Universal Authentication Framework), U2F (Universal Second Factor) and FIDO2. The most recent FIDO Alliance standard, FIDO2, enables password-less authentication for both mobile and desktop apps via mobile devices.
FIDO2 vs WebAuthn: The words FIDO2 and WebAuthn are not interchangeable. FIDO2’s key component is WebAuthn. The set of standards and APIs enables the browser to interact with the operating system and deal with cryptographic keys. WebAuthn is a FIDO2 standard, however, it was created by the W3C.
FIDO Advantages & limitations
The first major advantage and one of the defining features of FIDO is Password less Authentication. It minimizes the risk posed by the use of credentials, reducing vulnerability to stolen credentials, phishing, ransomware and other social engineering attacks, however, if you lose access to your device or FIDO key and the malicious actor knows your device pin or password they can access all those services that have FIDO authentication enabled through that device.
User Convenience and Interoperability are also the key advantages to prefer FIDO Authentication. But having a single key or device that can store multiple keys for various websites and apps also increases the harm that can be caused in case the key is compromised.
Conclusion
FIDO2 has become a standard accepted by major device makers and online platforms alike, with the key benefits being the simplicity of use, privacy, and security. It enables password-less authentication without storing cryptographic keys on a server, making credential compromise considerably difficult. Since 2012, the FIDO Alliance has been developing standards. Users may use their mobile devices to authenticate instead of a physical key in this latest generation. FIDO2 can help with access management. As password-less authentication gets popular, it will become even convenient.
How SecurDI Can help.
There are several tools and technologies available on the market to help organizations of all sizes safeguard themselves. However, in order to choose the best technology, you will need a team of experts. SecurDI’s experts have decades of experience in various cybersecurity domains and thus can help you navigate this process. Our mission is to become your trusted adviser and deliver solutions that help meet your business objectives.
Authored By – Amit Kr Sharma Cyber Security Junior Analyst

