The Power of Cloud
In today’s scenario, many organizations are increasingly moving to the cloud, most influential acceleration businesses underwent and undergoing. This is due to the many benefits that the cloud offers, the primary reasons being flexibility, scalability, and a pay-as-you-go model. As the digital economy is ever-changing, the cloud gives us greater insights in the case of large data ecosystems. The major concern of any organization whether it be on-premise or cloud, security is always a concern and has to be addressed. The fact that IT infrastructure is getting more hybridized and with so much growth and so much data, the number of breaches and attacks also increased.

Cloud Application Security Unveiled
Before we get into the aspects of the challenges faced in today’s scenario or how one can best protect it, a fundamental question has to be answered i.e. what does cloud application security mean and why is there a need to stress on application security over the cloud.
In simple terms, cloud application security is a set of policies and processes that enhance an organization to protect applications and data in a cloud or hybrid environment. As mentioned before, since there is a huge increase in organizations moving to cloud platforms, there are more dynamics in terms of critical data and network parameters. Though, in general, any cloud service provider offers a security solution for the respective platform but the security factor increases when there are multiple cloud providers involved in the scenario. According to a Gartner survey, more than 80% of public cloud users use multiple providers.
Cloud application security is critical for organizations that utilize collaborative online services like Slack, Microsoft Teams, or Box, as well as those that operate in a multi-cloud environment hosted by a third-party cloud provider like Amazon, Microsoft, or Google. While these services or apps are beneficial to the business and its workers, they significantly enhance the attack surface by giving numerous additional ports of entry for adversaries to infiltrate the network and launch assaults. Hence extra importance has to be given in such cases.
Now that the base definition has been established and there is a good understanding of what is cloud application security and its importance, the next big question is how can one achieve a robust security system for it, what are the possible challenges that can be faced and how can they be solved; all of which will be discussed in the upcoming section.
Hurdles faced
Any solution that is implemented in any organization, there will be challenges faced as each organization varies from each other. Especially, cloud applications are more vulnerable to a wide range of threats, and here are some common threats that an organization should consider while developing their cloud application solution.
- Misconfiguration: It is one of the most serious security threats to cloud applications and systems. It happens when users accidentally authorize external connection to network resources, allowing apps and servers that should not be privileged to access data and assets. Attackers have no difficulty taking advantage of those flaws by obtaining the login information of unsecured endpoints.
- Account Hijacking: Poor password security and data breaches frequently result in valid accounts being hacked. If an attacker breaches an account, they can access sensitive data and have total control over cloud assets
- Insecure APIs: APIs are frequently the sole assets in an organization that has a public IP address. As a result, they may be a convenient target for hackers, particularly if they are unsafe owing to inadequate access restrictions or encryption mechanisms.
- Lack of visibility: Due to the multi-cloud nature of many organizational systems, difficulties with cloud security are exacerbated further by the extensive administration of configurations, nuanced reporting over applications, and access control, which frequently results in fragmented processes including manual configuration and limited visibility.
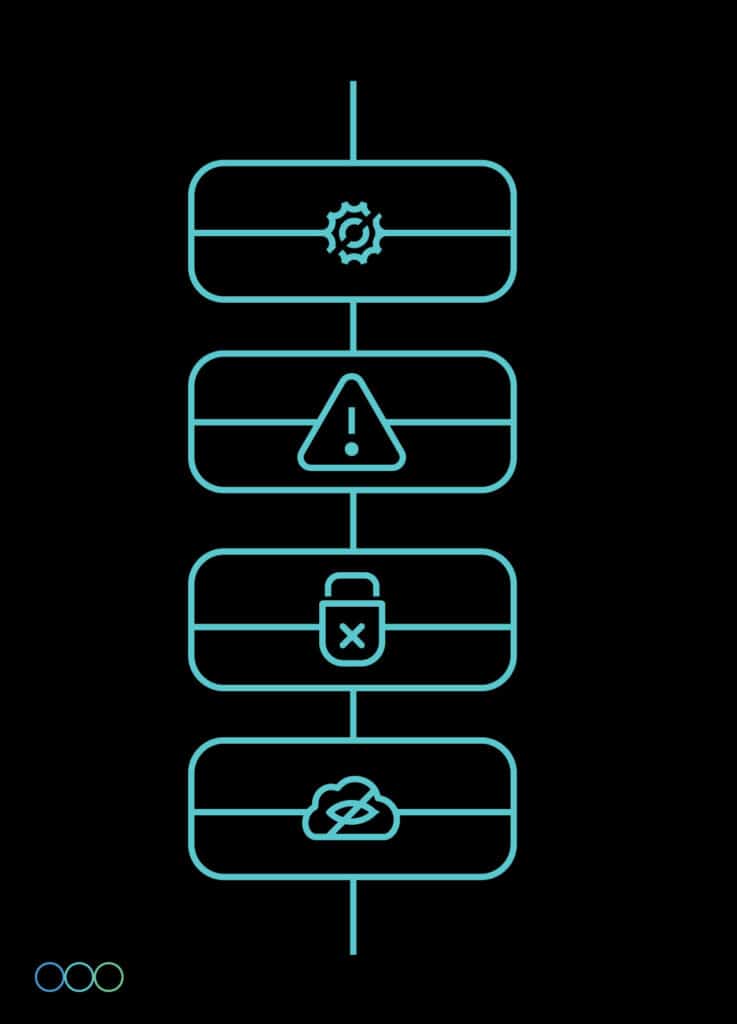

Cloud Application Security Framework
- CSPM: Using cloud security posture management (CSPM), an IT security solution, cloud-based systems, and infrastructure are monitored to identify potential vulnerabilities in cloud services, online applications, and resources, as well as misconfigurations and compliance violations.
- CWPP: The phrase “cloud workload protection platform” (CWPP) was first used by Gartner to describe a class of security technologies that guards workloads that are hybrid and multi-cloud, such as serverless operations, virtual machines (VMs), bare metal servers, and containers.
- CASB: In order to aggregate and insert enterprise security policies as cloud-based resources are accessed, Gartner defines a cloud access security broker (CASB) as an on-premises or cloud-based security policy enforcement point that is positioned between cloud service users and cloud service providers.
Safeguard your Cloud
Well, if any solution’s propaganda is that it will give 100% security is only possible in an ideal environment. At the end of the day, we are all humans and errors do tend to happen. Hence one cannot proclaim a solution to give full security. Still, there is a sure possibility to avoid as many errors as possible and make any organization shield itself from data breaches and cyber-attacks. So what are the steps to be followed/taken in order to have a robust security system.
- Invest more in the solution: Expansion and scalability are factors considered in the future roadmap for any organization. Now an individual can access networks and systems from any remote location, which paves the way for potential attack vectors from bad actors. Hence adequate firewall protection and cloud native security software have to be handled with careful consideration.
- Implement Identity access management (IAM) and Regular Audits: When it comes to application security, there are often many cases where data loss, insider threats, and employee negligence are the primary causes of it. Hence proper audits will give greater visibility on the access control.
- Automate process: Monitoring, issue response, and configuration for cloud applications should all be automated as much as feasible for businesses. Manual processes are prone to mistakes and frequently result in oversights or data leaks.
Password protection and awareness: Train employees and customers about the best practices about password policies which have high complexity with a good combination of special characters and numericals. As in most cases, phishing and social engineering is the starting point for an attack, following the best practices and leveraging MFA will eliminate most of the threats.
How SecurDI can help
We understand the paramount importance of application security in today’s cloud-driven landscape. With a team of seasoned experts and cutting-edge technologies, we are dedicated to helping you fortify your cloud-based applications against emerging threats. Whether it’s providing comprehensive security assessments, our tailored solutions will ensure that your applications remain resilient and protected in the cloud. Let us be your trusted partner in navigating the ever-evolving world of cloud computing security, so you can focus on what you do best – innovating and growing your business with confidence.

